Research and application of one card multi-purpose security smart card structure
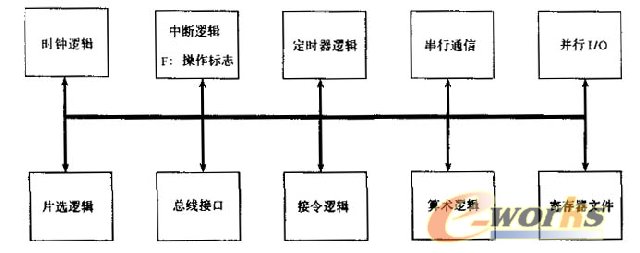
I. Introduction Figure 1 Chip structure of the new security smart card The CPU in the new type of security smart card is mainly composed of clock logic, interrupt logic, timer logic, serial communication, parallel I/O, chip select logic, bus interface, instruction logic, arithmetic logic, register file, etc. The CPU can adopt 8 Bit or 16 bits, it is best to use RISC technology and pipeline technology to improve speed, its hardware structure is shown in Figure 2. Figure 2 CPU structure of the new security smart card In order to support users to download programs, multi-purpose one card, and ensure the security of each user's data, multiple user areas must be isolated and protected. Address isolation allows different applications to be restricted to different areas to ensure data security. An operating flag and a hardware interrupt have been added to the CPU of the new smart smart card. The operation flag is used to distinguish whether the current operation mode is the system mode or the user mode. The new interrupt is used to notify the chip operating system to terminate the execution of the user command when the user of the application commands the address space of the system or other application. One of the methods for performing isolation protection between storage areas is to set address comparison registers for the corresponding storage areas, including memory address upper and lower bound address registers, program address upper and lower bound registers, and data address upper and lower bound registers. In user mode, program access is limited by the address compare register, and only the address space defined by the address compare register can be accessed. When a program in a certain area is executed, the memory address of the accessed area must be compared with the value of the upper and lower bound registers. If it is not out of bounds, it can be accessed. If it is out of bounds, it cannot be accessed and a hardware interrupt is generated, and the operating system will terminate. The execution of the program ensures that the user commands downloaded by a particular application can only access their own address space, and cannot access user commands or data of the system or other applications to achieve isolation protection between the storage areas. In system mode, program access is not restricted and the entire address space can be accessed. Figure 3 serial communication controller structure Because the internal structure of the CPU is reasonable, the main registers are software programmable, so the communication program will be very easy to write. Figure 4 chip operating system logic structure The communication management module: realizes the communication between the smart card and the reading and writing device according to the ISO 7816-3 standard, and ensures the correct transmission of commands and data. According to the user's request, you can choose the Yufu transmission protocol T=0 or the block transmission protocol T=1. Product categories of Women's Shoulder Bag, we are professional China manufacturer of all kinds of Bags, Polyester Shoulder Bag, Fashion Women's Shoulder Bag for women. The women's shoulder bag has women-specific shoulder straps with flexible attachment points are contoured for a women's torso for a perfect fit for any size or shape. The women's shoulder bag is simple, casual and fashionable with high quality. The women's shoulder bag has convenient magnet closure design and soft material, comfortable to carry. It's a good choice for traveling, working, shopping, school, etc. We have cooperated with many famous brands allover the world. We can do OEM or ODM for our customers. We have the perfect after-sales service and technical support. Contact us today to establishing new and goods business relationship. Women's Shoulder Bag Womens Shoulder Bag,Shoulder Hand Bag,Womens Shoulder Hand Bag,Pu Shoulder Bag Panway Industries Co., Ltd. , https://www.panwaybags.com
A smart card is a card with a microcontroller chip. Because the smart card contains CPU, rich hardware resources, and support from the chip operating system, it has high security. It has become an important security device, especially in today's rapid development of e-commerce, e-finance and e-government, smart cards. It will play an increasingly important role as a vehicle for identity vouchers, e-wallets, electronic passbooks and various certificates as well as important data.
Smart cards are rapidly evolving in a safe, high-speed, and convenient direction. As the demand for multiple cards and user download programs continues to increase, existing smart cards and their chip operating systems expose some security flaws. They either do not provide user download functionality, that is, provide a fixed operating system to all users, or allow users to download programs but only attempt to protect user data and its programs from software, such as users who perform download user commands. Identity authentication, only those users who have certain secret information can download user commands. However, security protection from the software perspective is not enough, and there are still security risks. On the one hand, an attacker may obtain such secret information through some channels, and on the other hand, it cannot prevent malicious users from having legitimate download rights. Once the user commands the download successfully, the chip operating system cannot monitor these downloaded user commands because the downloaded user commands are at the same level as the operating system, and the user commands are also implemented by the CPU's assembly instructions, as long as they are legitimate instructions, the CPU Will be executed. Because the instruction is the lowest level of the software, the chip operating system is also built on the instruction. This allows commands downloaded for a specific application to be accessed by programs or data from other applications. If an application download command contains instructions to tamper with another application's data, the chip operating system cannot control the execution of its instructions.
In order to overcome the above defects, this paper proposes a new type of security smart card structure, which has the following technical features:
· Support one card for multiple use, adapt to face width, easy to carry and manage.
· Support users to download programs, flexible and convenient to use.
· Different applications are protected by physical isolation to ensure data security.
· With a cryptographic coprocessor, the cryptographic operation speed can be greatly improved.
· U SB interface for easy electronic key function and high speed data transmission.
·There is a watchdog circuit inside, which has high system reliability.
This paper first discusses the structure principle of one-card multi-use security smart card from two aspects of software and hardware, and realizes the security scheme for isolating multiple application areas, that is, limiting the range of visits of specific user commands, and truly achieving protection for multiple application areas. Purpose, then discuss an application example of this new type of security smart card.
Second, the hardware structure of the new security smart card
The new security smart card first supports the isolation of multiple applications and ensures the security of user programs and data. It adds hardware interrupts, operation flags, and memory address compare registers, program address compare registers, and data address compare registers. The new security smart card chip consists of CPU, various memories (RAM, ROM, EEP-ROM, Flash Memory), crypto coprocessor, serial communication, address isolation and interrupt control logic. The hardware structure is shown in Figure 1. . 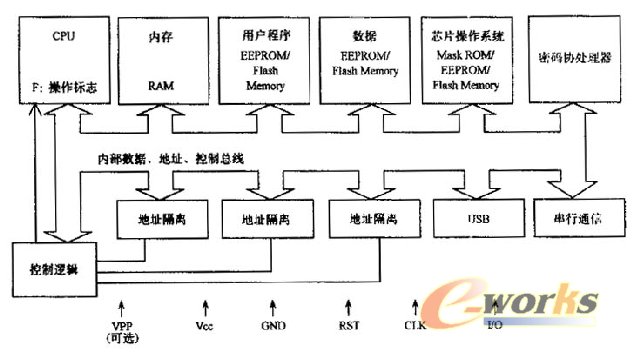
The values ​​of the upper and lower bound registers are software configurable and are managed by the chip operating system, which is flexible and convenient. Moreover, each type of comparison register only needs a pair of upper and lower bound registers to achieve isolation protection of multiple application storage areas.
With the popularization and application of network technology, due to the inherent openness, borderlessness and freedom of the Internet, network security, especially the identification of identity, electronic signature, data encryption, etc., have become a concern. a focus. The USB interface is designed in the new safety smart card to facilitate electronic key function and high-speed data transmission.
In the new security smart card, the ROM space is used to store COs and some fixed data. The RAM space is used to store interrupt vectors, system stacks, and intermediate data. EEPROM/Flash Memory is used to store system data, user programs, or user data.
To ensure data security, digital signatures must be implemented in smart cards. Digital signatures can be implemented with public key cryptography RSA and ECC. Whether it is RSA or ECC, its calculations are extremely complicated. Relying on 8-bit or 16-bit CPUs to implement RSA and ECC software, the speed will be very slow. In order to increase speed, hardware support is required. Therefore, a cryptographic hardware coprocessor is designed in the smart card to suit the application of the smart card.
Serial communication logic supports smart card communication for a variety of protocols. The CPU provides a full-duplex bidirectional communication controller whose logical structure is shown in Figure 3. 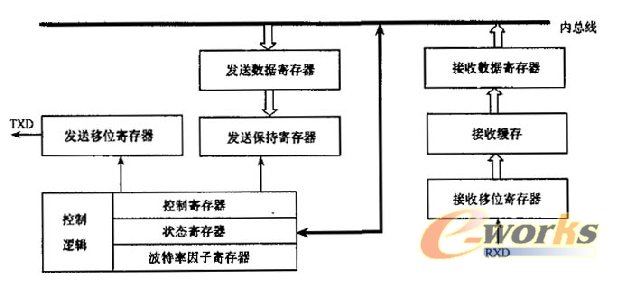
Third, the new security smart card chip operating system structure
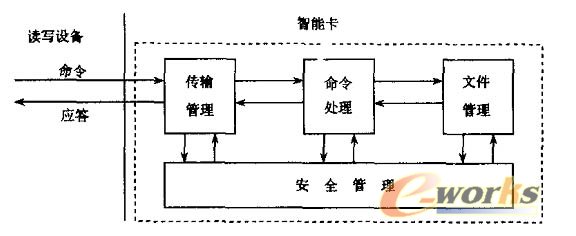
The operating system of the smart card (referred to as COS) is the basis for the management and security of smart card resources. It consists of four functional modules: transmission management, file management, security management, and command processing, as shown in Figure 4.